A leaky database of SMS text messages exposed password resets and two-factor codes
A security lapse has exposed a massive database containing tens of millions of text messages, including password reset links, two-factor codes, shipping notifications and more.
The exposed server belongs to Voxox (formerly Telcentris), a San Diego, Calif.-based communications company. The server wasn’t protected with a password, allowing anyone who knew where to look to peek in and snoop on a near-real-time stream of text messages.
For Sébastien Kaul, a Berlin-based security researcher, it didn’t take long to find.
Although Kaul found the exposed server on Shodan, a search engine for publicly available devices and databases, it was also attached to to one of Voxox’s own subdomains. Worse, the database — running on Amazon’s Elasticsearch — was configured with a Kibana front-end, making the data within easily readable, browsable and searchable for names, cell numbers and the contents of the text messages themselves.
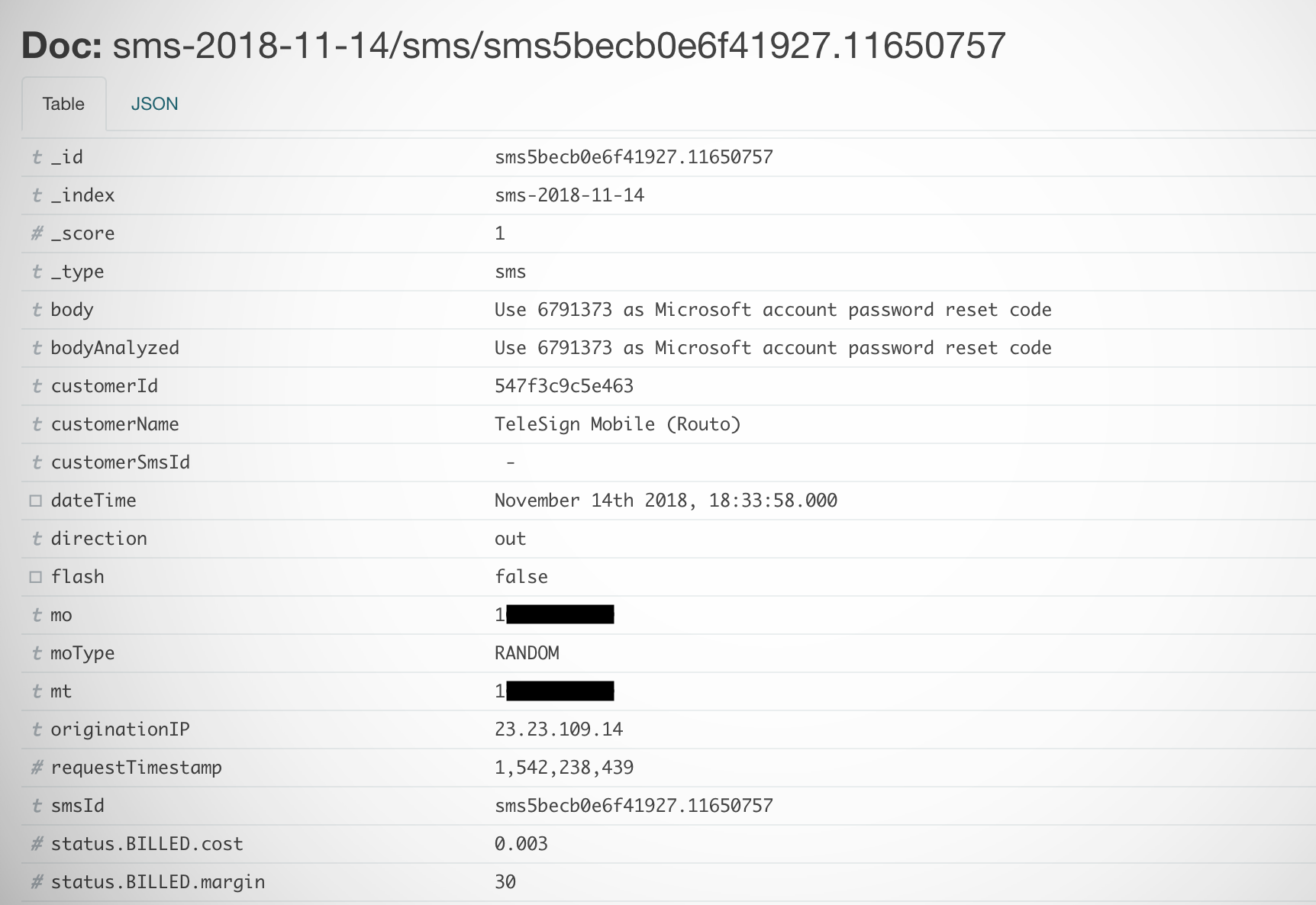
An example of one text message containing a user’s phone number and their Microsoft account reset code. (Image: TechCrunch)
Most don’t think about what happens behind the scenes when you get a text message from a company, whether it’s an Amazon shipping notification or a two-factor code for your login. Often, app developers — like HQ Trivia and Viber — will employ technologies provided by firms like Telesign and Nexmo, either to verify a user’s phone number or to send a two-factor authentication code, for example. But it’s firms like Voxox that act as a gateway and converting those codes into text messages, to be passed on to the cell networks for delivery to the user’s phone.
After an inquiry by TechCrunch, Voxox pulled the database offline. At the time of its closure, the database appeared to have a little over 26 million text messages year-to-date. But the sheer volume of messages processed through the platform per minute — as seen through the database’s visual front-end — suggests that this figure may be higher.
Each record was meticulously tagged and detailed, including the recipient’s cell phone number, the message, the Voxox customer who sent the message and the shortcode they used.
Among our findings from a cursory review of the data:
- We found a password sent in plaintext to a Los Angeles phone number by dating app Badoo;
- Several Booking.com partners were sent their six-digit two-factor codes to log in to the company’s extranet corporate network;
- Fidelity Investments also sent six-digit security codes to one Chicago Loop area code;
- Many messages included two-factor verification codes for Google accounts in Latin America;
- A Mountain View, Calif.-based credit union, the First Tech Federal Credit Union, also sent a temporary banking password in plaintext to a Nebraska number;
- We found a shipping notification text sent by Amazon with a link, which opened up Amazon’s delivery tracking page, including the UPS tracking number, en route to its destination in Florida;
- Messenger apps KakaoTalk and Viber, and quiz app HQ Trivia use the service to verify user phone numbers;
- We also found messages that contained Microsoft’s account password reset codes and Huawei ID verification codes;
- Yahoo also used the service to send some account keys by text message;
- And, several small to mid-size hospitals and medical facilities sent reminders to patients about their upcoming appointments, and in some cases, billing inquiries.
“Yeah, this is very bad,” said Dylan Katz, a security researcher, who reviewed some of the findings.
The exposure to personal information and phone numbers notwithstanding, the ability to access two-factor codes in near-real-time could have put countless number of accounts at risk of hijack. In some cases, websites will only require a phone number to reset an account. With access to the text message through the exposed database, hijacking an account could take seconds.
“My real concern here is the potential that this has already been abused,” said Katz. “This is different from most breaches, due to the fact the data is temporary, so once it’s offline any data stolen isn’t very useful.”
Kevin Hertz, Voxox’s co-founder and chief technology officer, said in an email that the company is “looking into the issue and following standard data breach policy at the moment,” and that the company is “evaluating impact.”
Many companies, including Facebook, Twitter and Instagram, have rolled out app-based two-factor authentication to thwart SMS-based verification, which has long been seen as vulnerable to interception.
If ever there was an example, this latest exposure would serve well.











