Tag Archive for: security
RunBMC: OCP hardware spec solves data center BMC pain points
Security
Eric Shobe and Jared Mednick Yesterday
Open source is not just for software. The same benefits of rapid innovation and community validation apply to hardware specifications as well. That’s why I’m happy to write that the…
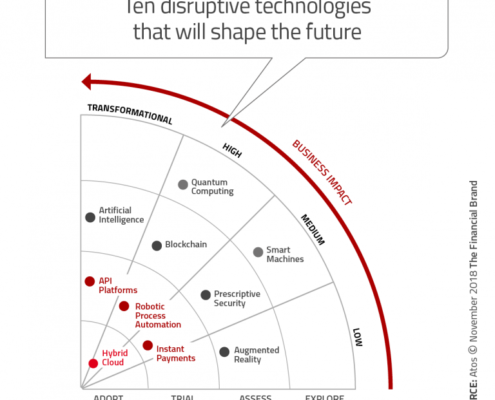
10 Technologies That Will Disrupt Financial Services In The Next 5 Years
Business Intelligence, Innovative Ideas, Productivity, Security
SUBSCRIBE NOW GET THE FINANCIAL BRAND NEWSLETTER FOR FREE - SIGN UP NOW
The scope and speed of evolution in regulation, customer behavior and technology – coupled with the emergence of new competitors – mean that the future of banking…

One issue is probably to blame for your IT outages and data losses – and it’s not hackers
Managed Network Services, Security
The main causes of downtime remain prosaic, but cyber incidents are growing too.
By Steve Ranger | July 11, 2019 -- 14:38 GMT (07:38 PDT) | Topic: Security A hardware failure is most likely to cause unexpected downtime…

21 technology tipping points we will reach by 2030
Business Intelligence, Innovative Ideas, Managed Network Services, Productivity
Cadie Thompson,
Tech Insider
Shutterstock/GaudiLab
Nov. 12, 2015, 1:57 PM
From driverless cars to robotic workers, the future is going to be here before you know it.
Many emerging technologies…

An industrial manufacturing perspective: Tech Trends 2019
Business Intelligence, Innovative Ideas, Productivity, Security
Deloitte
Beyond the digital frontier
How can industrial manufacturers keep pace in a quickly evolving industry? By tackling transformation head-on and embracing change. As technology trends reshape how value is delivered to…

Week in Breach
Managed Network Services, Security
This week, credentials from the Dark Web compromise a company's network, healthcare records are held for ransom, and data breaches become more expensive.
Dark Web ID Trends:
Top Source Hits: ID Theft Forums
Top…

Week in Breach
Managed Network Services, Security
The Week in Breach: 07/17/19 - 07/23/19
By Kevin Lancaster on Jul 24, 2019 4:42:02 PM
This week, hackers send a message to government agencies, employee errors compromise thousands of people’s data, and Australians demand data security…

How to use Alexa and still keep your privacy
Business Intelligence, Security
Update your Amazon Alexa settings to make your smart speaker a bit more secure.
BY
MEGAN WOLLERTON
APRIL 25, 2019
Smart speakers add a level of convenience to daily life, but there…

The Week in Breach
Managed Network Services, Security
United States - NEO Urology
Exploit: Ransomware
NEO Urology:…

Cyber Heist News
Security
[Heads-up] The U.S. Launched A Cyber Attack On Iran, And We're Expecting Spear Phishing Strike Backs CyberheistNews Vol 9 #26 | June 24th., 2019 [Heads-up] The U.S. Launched A Cyber Attack…
